Overview
testssh.sh is a free command line tool that will check the TLS/SSL cyphers and protocols within a server’s service on any port. It will also provide information about recent cryptographic flaws, vulnerabilities, and additional information.
This tool comes as a part of the Kali Linux distribution that we commonly use for security penetration testing, which also comes with many security tools. However, it can be run on any Unix-like platform and Windows using Docker or Cygwin.
Install testssl.sh
If you have a Linux distribution, you can clone the GitHub repo to your local Linux box using the git clone command.
git clone --depth 1 https://github.com/drwetter/testssl.sh.git
dhananjak@ansible-core ~]$ git clone --depth 1 https://github.com/drwetter/testssl.sh.git
Cloning into 'testssl.sh'...
remote: Enumerating objects: 106, done.
remote: Counting objects: 100% (106/106), done.
remote: Compressing objects: 100% (99/99), done.
remote: Total 106 (delta 14), reused 40 (delta 7), pack-reused 0
Receiving objects: 100% (106/106), 8.73 MiB | 3.52 MiB/s, done.
Resolving deltas: 100% (14/14), done.
[dhananjak@ansible-core ~]$ cd testssl.sh/
[dhananjak@ansible-core testssl.sh]$ ls
bin Coding_Convention.md CREDITS.md Dockerfile Dockerfile.md LICENSE Readme.md testssl.sh
CHANGELOG.md CONTRIBUTING.md doc Dockerfile.git etc openssl-iana.mapping.html t utils
[dhananjak@ansible-core testssl.sh]$
Or if you have installed Docker or Podman in your operation system (Linux or Windows), you can execute the below Docker command to run the testssl.sh container image in your local workstation.
docker run --rm -ti drwetter/testssl.sh <your_cmd_line>
[dhananjak@ansible-core testssl.sh]$ podman run --rm -ti drwetter/testssl.sh
✔ docker.io/drwetter/testssl.sh:latest
Trying to pull docker.io/drwetter/testssl.sh:latest...
Getting image source signatures
Copying blob ee01184df9f8 done
Copying blob e585601fa46b done
Copying blob 4fabb917626b done
Copying config 2bee4e4cab done
Writing manifest to image destination
"testssl.sh [options] <URI>" or "testssl.sh <options>"
Execute the testssl.sh
This is one of the easiest pen-testing tools to utilize and provides valuable information about your web site or application.
In order to get started, change to the directory where the testssl.sh script is located. Let’s run these commands to see what will happen:
Standard HTTPS web server:
./testssl.sh https://<IP Address or Domain name>
Non-standard SSL ports:
./testssl.sh <IP Address or Domain name: Port>
Let’s run this script against the Google.com domain and see what happens.
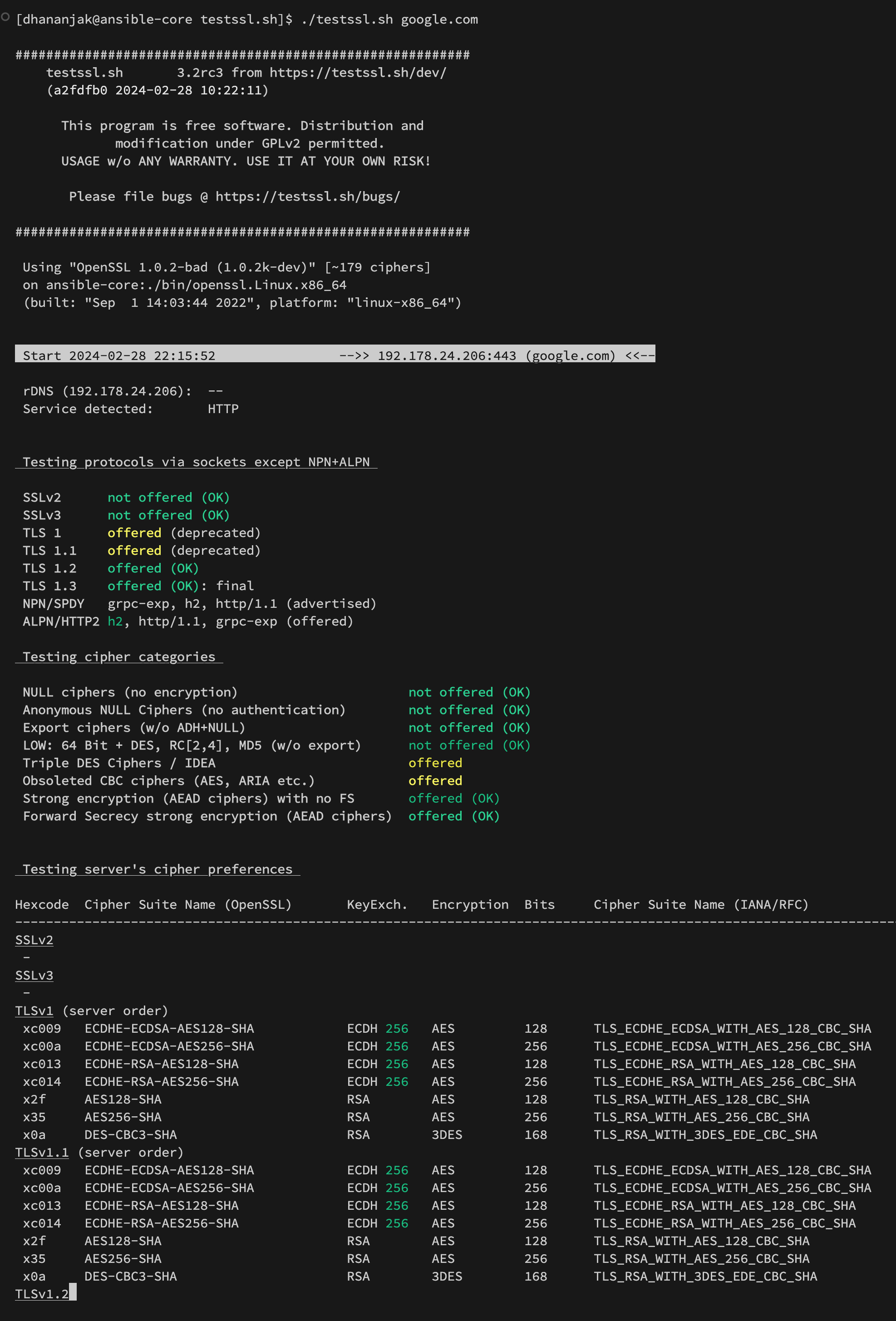
You can see all the information about the website, TLS/SSL information, and much more.
If you use the Docker container image, you can execute the following command against any URL.
podman run --rm -ti drwetter/testssl.sh google.com

Check Common Vulnerabilities
For example, you want to check whether your web server is vulnerable to LUCKY13 attacks. Then, you can use a single check command to validate your web server.
./testssl.sh -q -L google.com
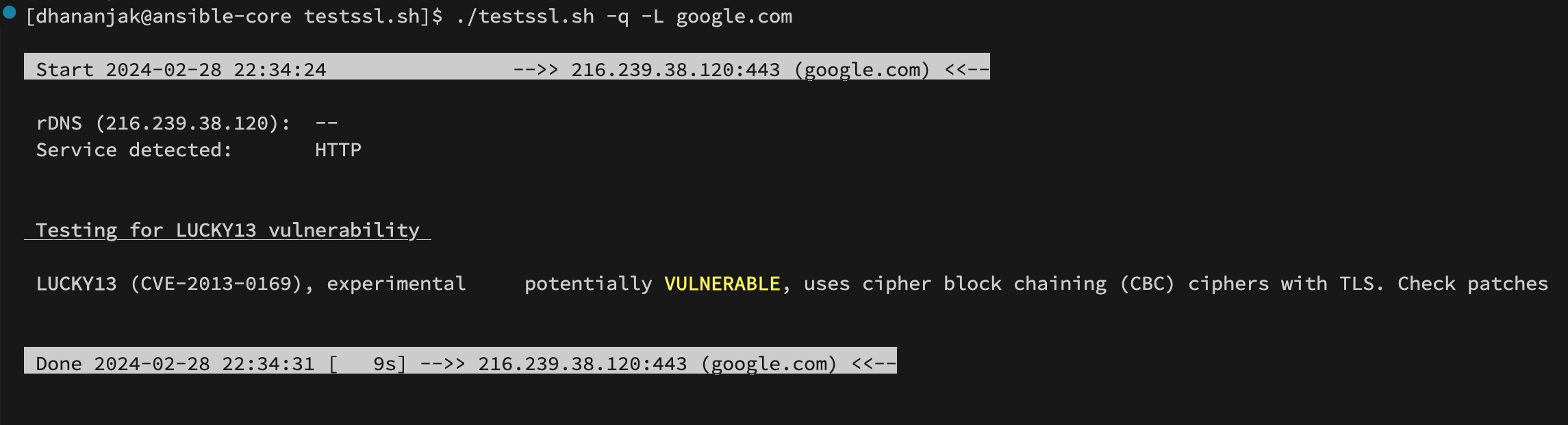
Likewise, you can pass many flags based on your need to retrieve your web server’s information. You can execute the below command to check all parameters and it will give you a general idea of how to use it:
./testssl.sh --help
Conclusion
As you read this blog post, you will hopefully see how easy it is to install and use testssl.sh for testing every day. If you want to learn more about this toolset, visit their website at https://testssl.sh/ for further information. I would like to conclude by saying that many tools perform similar tests. For reporting purposes, testssl.sh provides clear output for reporting purposes, which makes it valuable.